
BLOG
Phishing emails: how to recognize them and avoid being scammed
Phishing emails are a common threat in today's digital world. Learn how to identify them and protect your personal information with our comprehensive guide to recognizing and avoiding phishing scams.

Today the Internet is our constant assistant in life and work. However, with its development, threats have also grown, among which phishing is especially dangerous. Learning how to protect yourself from this type of online scam is essential because phishing emails often look very believable, sometimes even with a personal message. Since all of us will experience a phishing attack at some point or another, it's important to know what signs to look out for. Online fraud has become a daily problem, and identifying phishing scams is sometimes harder than it seems.
Phishing: what is the problem?
Online scammers around the world use phishing to scam their victims out of bank details, passport details and other important information. Methods are becoming increasingly sophisticated: attackers can impersonate your colleagues, bank employees, or even government officials. By clicking on a phishing link, you risk becoming another victim of these scammers.
Before we talk about protection methods, let's answer a few important questions:
What types of phishing are there?
What should I do if I received a phishing email?
Can I become a victim of a phishing attack?
How to recognize a phishing email?
How to prevent phishing?
What is phishing?
Phishing is a type of scam in which an attacker tricks you into performing an action that allows them to gain access to your device, accounts, or personal information. Scammers pose as people or organizations you trust to infect your device with malware or steal your banking details. In other words, using social engineering techniques, they hook you into trusting you to gain valuable information. This can be any information: from a social network account to passport data.
Scammers trick you into opening an attachment, following a link, filling out a form, or giving them your information. Therefore, it is important to always be on your toes, even though it can be tiring.
How does phishing happen?
The most common phishing scenario looks like this:
You receive a notification email from your bank. Clicking on the link takes you to a fake web page that looks like your bank's website.
On this page you are asked to confirm your username and password. By entering this data, you are passing it on to scammers.
You are redirected to the bank's real website, and you enter your data again, unaware that it has already been stolen.
Phishing attacks can also be carried out through phone calls. Fraudsters can be very creative and use any communication channels to trick you into giving you information.
How to protect yourself from phishing?
To avoid becoming a victim of phishing, you need to know how scammers operate and how to recognize their attacks.
Who is at risk of becoming a victim of phishing?
Anyone can become a victim of a phishing attack, regardless of age or place of work. Fraudsters find their victims' contact information in the public domain and include them in their lists for phishing attacks. It is important to be attentive and careful so as not to become easy prey for Internet scammers. How to recognize and avoid phishing emails
Nowadays, it is difficult to hide your phone number, email address, messenger IDs or social media accounts. Therefore, the chances of becoming a target for an attack through one of these channels are high. Moreover, scammers can target their phishing attacks both at a general audience and at specific individuals.
Phishing through spam mailings
Phishing through spam mailings is a wide-spread network that anyone can fall into. Most phishing attacks fall into this category. Spam is the electronic equivalent of paper advertising, but much more dangerous because it can be part of a phishing scheme.
Fraudsters and cybercriminals send out phishing spam en masse to:
To extract money from at least a small number of recipients who responded to the message.
Fraudulently obtain passwords, card numbers, bank details and other information.
Inject malicious code into victims' devices.
Phishing through spam emails is one of the most common ways to obtain data, but some attacks have a more precise target.
Spear phishing
Spear phishing, also known as spear phishing, and its variant, whaling, target specific people. Whaling targets high-level individuals, while spear phishing targets a wider range of people, including employees of businesses or government organizations. Fraudsters may target you if you are a client of a bank they are interested in or an employee of a medical institution.
Fraudsters carefully prepare these personalized attacks by collecting information from:
Profiles on social networks.
Leaked data.
Open sources.
They can attack quickly, prompting you to take immediate action, or build relationships over months to build trust before the decisive move. Fraudsters use all communication channels, including hacking legitimate sites, so it is important to be careful.
Types of phishing
Phishing attacks can be carried out in different ways:
Email phishing. Emails asking you to follow a link, make a payment, or open an attachment. The sender's address may appear to be genuine.
Domain name spoofing. Fraudsters imitate genuine email addresses by slightly changing them.
Voice phishing (vishing). Calls from fake numbers where scammers pretend to be real people or companies.
SMS phishing (smishing). Messages asking you to follow a link or call a number issued for an urgent problem.
Phishing on social networks. Traps in posts or personal messages, often disguised as attractive offers.
Clone phishing. Fraudsters copy real emails and replace attachments and links with malicious ones. This can happen through email or fake social media accounts.
Watering hole. Fraudsters exploit vulnerabilities on popular websites to distribute malware and redirect to malicious pages.
Pharming. Attackers redirect traffic from a secure site to a phishing page by exploiting malware or site vulnerabilities.
Typsquatting. Fraudsters create fake websites with addresses similar to real ones, trapping users with typos.
Clickjacking. Using website vulnerabilities to embed hidden traps that intercept logins, passwords and other information.
Tabnabbing. The fraudulent page reloads to a password entry page, simulating a legitimate site.
HTTPS phishing. The fraudulent page masquerades as a secure website using a padlock icon in the address bar.
Additional types of phishing
"Evil twin" Fraudsters create fake Wi-Fi networks in public places to intercept user activity.
Phishing in search engines. Manipulating search results so that fake pages appear first.
Angler phishing. Fraudsters pretend to be customer support staff on social media.
Breaking corporate mail (Business email compromise, BEC). Hacking corporate communication channels to obtain valuable information.
Cryptocurrency phishing. Fraud targeting crypto wallet owners.
Be careful and careful not to fall for the tricks of scammers.
Variety of phishing attacks and methods of protection
There are many types of phishing, and their number is constantly growing. We have described the most common types of attacks today, but new ones may appear in the near future.
Signs of Phishing and Precautions
Phishing emails may look real, but there are ways to spot them:
Check the sender's email address. For example, WHO staff addresses end in @who.int, not @gmail.com.
Please check the link before clicking. Make sure the address starts with https://.
Be careful with personal information. Never share your information with third parties, even if it seems reliable.
Avoid haste and panic. Scammers often try to make you panic in order to get you to click a link or open an attachment.
If you receive a suspicious email, do not click on any links or enter personal information. Contact the relevant authorities or your bank to confirm the legitimacy of the request. Use only trusted websites and resources.
Actions to take when confidential information is disclosed and signs of phishing emails
What to do if confidential information is disclosed
Do not panic. Update your credentials on all sites where they may have been used. Change your passwords and contact your bank immediately.
Report fraud. Always notify the appropriate authorities of fraud attempts.
Signs of phishing emails and protection methods
Phishing emails have common signs that those who know what to look for can spot. These signs are not always obvious at first glance, so it is important to recognize them.
How to recognize a phishing email
To spot a phishing email, you need to pay attention to any unusual or illogical details. Let's divide the signs into main categories:
Presence of attachments or links.
Errors and typos.
Incorrect grammatical structures.
Unprofessional graphics.
Requiring you to immediately confirm your email address or other personal information.
Impersonal address, for example, “Dear customer.”
Attackers may be in a hurry to launch phishing sites, which can cause the sites to look significantly different from the real thing.
Example of analyzing a suspicious letter
Let's say you receive an email asking you to help hurricane victims, sent from the address "help@technicalsupport.ru". Although it may look like a legitimate organization, you should be careful, especially if you have never heard of it. Spam filters can sometimes miss such emails.
If you understand computer security, you won't immediately respond to requests for personal or financial information from unknown senders. It is important not to take hasty actions.
Actions to take when receiving a phishing email
Delete the email without opening it. Viruses can be activated when you open an attachment or click on a link. It is better not to open suspicious emails at all.
Block the sender manually. If possible, add the sender's domain to your blocked list, especially if other family members use the mailbox.
Add an extra layer of protection. Consider installing antivirus software for added security.
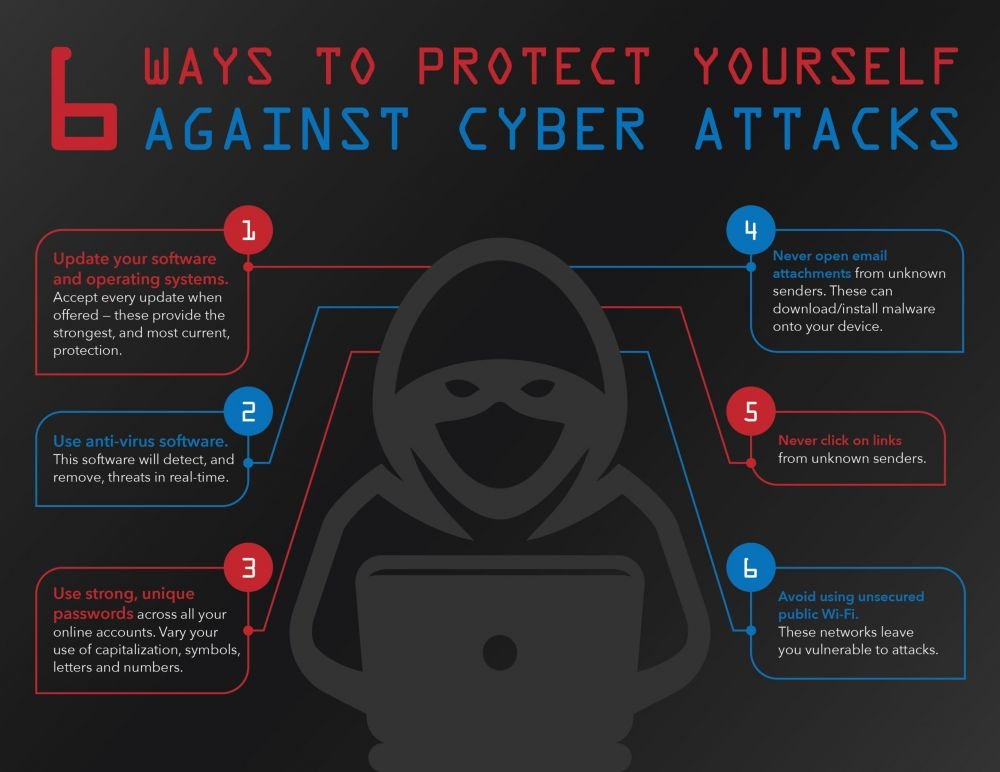
Recommendations for protection against phishing
Even if you receive phishing emails every day, most of them automatically end up in spam. Users have learned to recognize such letters and follow common sense.
However, phishing attacks can be insidious and use different communication channels. Following a few simple guidelines will help reduce your risk of becoming a victim:
Be attentive to unusual details in letters.
Do not click on suspicious links or open attachments.
Check the sender's address and links for authenticity.
Install antivirus software and update it regularly.
Report suspicious emails to the appropriate services.
Following these simple precautions will help you protect yourself from phishing attacks and other cyber threats.
Frequently Asked Questions about recognizing and avoiding phishing emails
How can I help others avoid phishing attacks?
To help others avoid phishing attacks, it is important to educate them on the signs and tactics of phishing, share experiences and security tips, and provide information about phishing techniques and current threats through educational campaigns and community outreach.
What advice can be given when a phishing email is detected?
When a phishing email is detected, it is important not to panic but instead to check it for signs of spoofing, avoid clicking on suspicious links and avoid providing personal information. You should also report the phishing attempt to the email administrators or the company whose name has been spoofed.
What steps can be taken to avoid falling into the trap of phishing emails?
To avoid fraud via phishing emails, educate yourself and your employees about security, do not open attachments or links from suspicious sources, be careful when providing personal information, and use multi-factor authentication where possible.
What signs can you recognize to determine that an email is a phishing email?
Some signs of phishing emails include strange sender email addresses, grammatical or spelling errors, demands for sensitive information or personal data, and threats or urgent demands.
What are phishing emails and what is their purpose?
Phishing emails are fraudulent messages designed to trick recipients into obtaining sensitive information such as passwords, credit card numbers, and personal information. The goal of phishing emails is often to steal personal or financial information
More from the BCG blog
Protection against Cyber Attacks: Guaranteeing Security in the Internet World
What to do if your business is subject to a cyber attack? find out about main steps that will help to you fast to react on threats and minimize damage . Our recommendations will help to you stay ahead cybercriminals .
5 May 2024


